TL;DR Link to heading
By using the search function in the mail with an empty search string, I retrieved all the usernames, for which I then checked if the password is the same as the username. By filtering out all the numeric usernames, I made sure I had excluded student accounts.
General Link to heading
After discovering a lot of vulnerabilities in the software itself, I went ahead and tried to get some other sort of vulnerabilities.
When I figured that there might be some development accounts for testing purposes, I started to look for places that might give me the names of these accounts. I found some endpoints that take usernames and return some info about the user. I could have used this to brute force the most common names, but then I discovered something better.
I stumbled upon a search function in the mail section which, supplied with an empty search parameter, returns all the usernames. Nice! Now lets quickly filter out all the real users, by removing all the numeric usernames. Next off, I wrote a small python script that tries to login with all the left over usernames, with the username as password. e.g. admin:admin. Lets run the script:
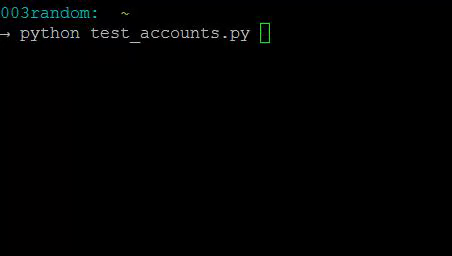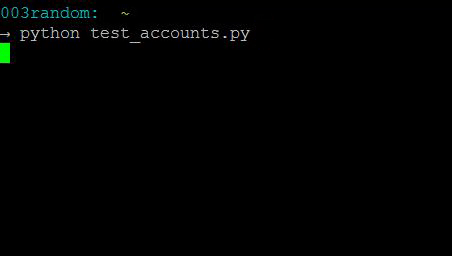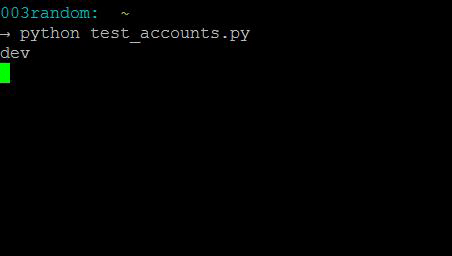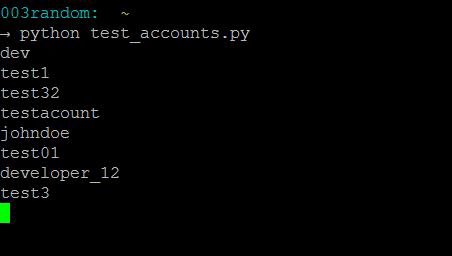
Wow! The accounts kept rolling in. After a couple of hours it finished with around 1700 test accounts. O.o Oke… So we’ve got a ton of accounts, now what?
Escalating Link to heading
I created a script that checks if the user account has permission to visit a given URL/web-service. This way we could easily check if an user has administrator rights or not. After running the script, it turned out that some test accounts had administrator rights. These accounts had the privileges and option to switch session to any user. (an administrator support option) So we escalated it to account takeover 🙂
Extra Link to heading
The python scripts I made are hosted on my GitHub: https://github.com/003random/PyScripts